Introduction
Overview
Admins are the managers of the system. What makes a user an admin is the power of permission over specific tasks and features.
The Management tab can be learned quickly. Learning to use all features together enables the flexibility of tiCrypt infrastructure.
A powerful mechanism in tiCrypt is the variety of workflows that can achieve similar objectives.
- Admins can control permissions per user with
User Profiles. - Admins can make announcements from the
Management tabor export tables in XML format.
tiCrypt does not give the admins full control over the system, but rather permission-based settings per user.
Super-admins have system responsibilities while sub-admins have team responsibilities.
The most sensitive permissions come with Projects and Virtual machines.
The role of a good tiCrypt admin implies awareness of user permissions, projects, and virtual machine management.
Admin Viewpoints
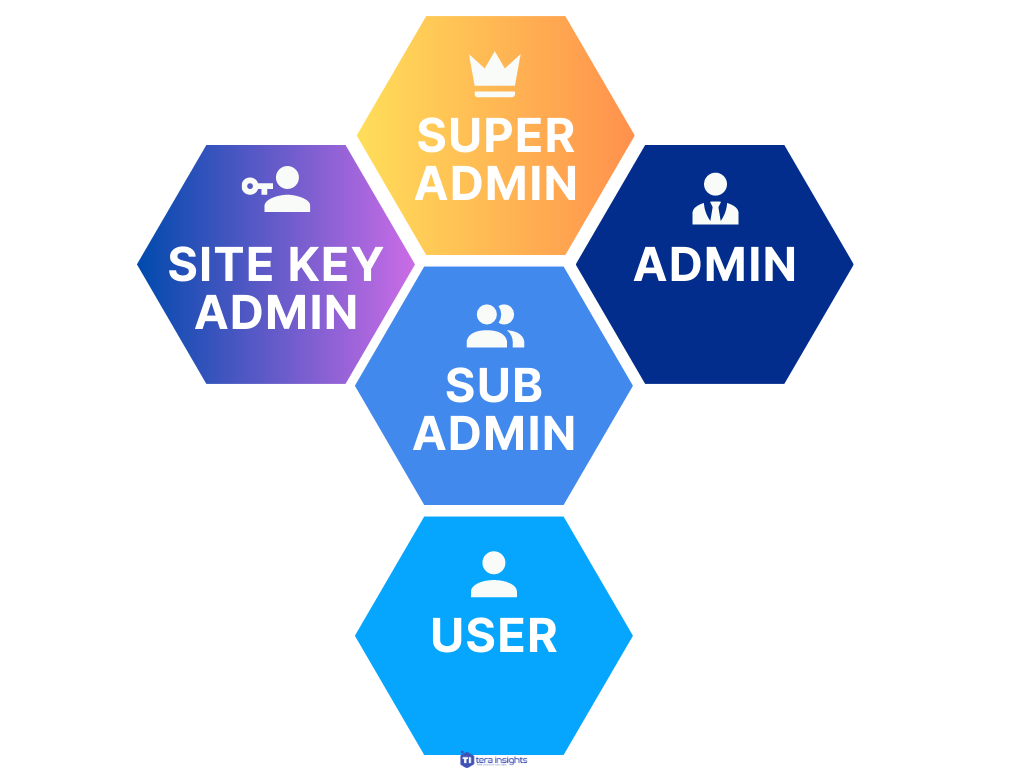
Admins Classification
Super-Admin
- Can change anyone's
permissions. - Has access to
system settings. - Has access to
global settings(i.e., add external servers, change key caching policy).
Admin
- Similar to Super-admin except:
- Cannot change/modify
global settings. - Cannot stop/restart
system services(and microservices). - Cannot modify super-admin settings.
- Cannot change/modify
Sub-Admin
- Manages and modifies
user permissionsandprojectsunder their own team only. - Can have multiple sub-admins in the same team. e.g., ABC Team as preferred.
System Management Map
tiCrypt management is mostly automated removing the burden of team management or the need of high technical expertise.
Hardware and networks are Virtual machine-based ensuring an isolated and secured user environment.
The system monitors all actions via tiAudit. Any troubleshooting attempt is considered a security threat that will prompt the admin to re-enter their password. Admins can perform checks with the audit team. This event will perform checks within the application using the system services option in the settings.
If an issue occurs it can usually be solved within minutes due to the alerting structure of the system. tiCrypt not only alerts unusual activity but also automatically blocks the whole spectrum of action.
Virtual machines function on isolated single ports to the local machine without any internet connection. This architectural tunnel avoids any data leakage or penetration possibility.
Users still have internet connection, aka their local machines.
Management operations are cryptographically secured and access-controlled. For example, Groups and VMs are cryptographic, while Teams and Projects are access-controlled.
tiCrypt goes beyond access control and cryptography, allowing a combination of access control and cryptography in a single container for doubled security.
The current infrastructure of Virtual Machine Hosts allows full housing for ITAR, FISMA, Medical Research, DoD projects, and other similar field research deployments.
Filtering power
tiCrypt management system can filter anything from users, teams, and groups to projects, classified projects, workflows, and complex infrastructure designs.
Criteria may be customized in the management tab, which uses the tiCrypt esoterical backend. This operation does not tire the system in any way.
tiCrypt can filter security. i.e.: Have a project unlocked or access controlled, or access control + cryptographically secured at the same time.
CSV & JSON Exports
Apart from the System Settings tab, all management sections in the management tab have CSV Export option and JSON Export option. Additionally, all actions and exports are permanently tracked in the tiCrypt auditing system.
Data Refresh
Users can use the Refresh option to reload the data within tiCrypt, for easy functionality and convenience. This command allows updates to be seen without re-login into the system.
Setting up accounts
Users receive a patch and installation instructions. They press the Next button several times, and the tiCrypt Connect is installed on their local machine.
After they click a button to generate their private key, they put their email and password on the registration page. This action will make them show up in the database as new and unactivated users.
Admin's responsibility is not installing tiCrypt on user's machines, but rather clicking for once activate user in bulk in the User section in the tab.
Workstations
System admins have the tools to build what is called Constellations where multiple VMs work together with the server to delegate resources between them automatically. In addition, they are all connected to one VM, which communicates with both VMs and their drives through a single virtually cryptographically encrypted VPN.
tiCrypt uses realms, which may be in Libvirt or AWS depending on the system preferences.
Firewalls and Backups
Admins can back up or never back up drives. Backup changes are recorded in the audit logs. The system may perform both full and incremental backups using Boolean values for custom data points.
An audit log is a record of a backup; a backup drive is the saved data itself.
Accounts Recovery
Systems are usually penetrated using the forgot my password option. tiCrypt has an escrow mechanism that ensures full security during a private key
recovery via the public key + the site key + escrow key, the sum of multiple escrow members' keys, and a digitally signed key from Tera Insights and the Super-admins.
The system forces members to communicate traditionally to prevent impersonation and social engineering attacks. The process has a simple UI requiring four recovery steps for lost account access.
Read more about escrow in the Escrow Role section.
Operating Systems
Linux and Windows are part of the tiCrypt interface. Admins can select their preferred system.
New Releases
Updates are conducted systematically and automatically.
Admins can switch to older versions at any time; however, they should keep the last updated version of tiCrypt due to usability and new upcoming features. Both admins and users can update tiCrypt by clicking on the last available version in tiCrypt Connect before logging in.
Auditing
tiCrypt Audit was built with the purpose of compliance. The goal of tiAudit is to keep track of all actions in the main system and make the system engineer and the audit team fully aware of what is happening in real time.
tiAudit is a separate system from the main system, therefore, audit users log in separately. Every action is audited from the installation day of tiCrypt until the present moment. Audit logs cannot be discarded due to high security.
Admin Ethics
Management with Users
tiCrypt management structure was primarily developed for users giving them an easy time carrying out both simple and complex projects. Admins are not needed to manage the system but rather to:
- Build workflows
- Oversee the system
- Check audit reports once a month
- Assist users on rare occasions
Users never see the coding in the front end; they are not forced to use command lines to navigate within their vault or virtual machine environments. tiCrypt UI was developed by researchers for researchers.
Reporting to Chief Technology Officer
Management in tiCrypt can afford direct reporting to decision-makers at anytime. System admins can generate an audit report by pressing a button. The results will showcase how users behaved if they did their homework and how far the system infrastructure evolved from the installation day.
This operation allows comprehensive system data forecasts. , i.e., if a user does X repeatedly in the future, it will trigger a Y trend in the infrastructure.
The Escrow section from the tab can be found in the escrow role - ticrypt admin section.