Who decides which users can share a file?
The user via their public-private key pair and the admin via access-controlled sharing permissions.
Sharing is a cryptographic key exchange only possible when the user receives access to the resource key and has the permission to share.
This action is based on the tiCrypt principle: Effective access.
To Remember
- Sharing is the intersection of who is allowed to share (access control) AND who has the resource key. (cryptographic).
- Each resource is encrypted with randomly generated AES-256 keys.
- Every resource has its own uniquely generated resource key made of the private key and public key of the user who created it.
When sharing a resource which has its resource key:
- You only decrypt the resource key with your
private key. - You encrypt the resource key with the user's
public keyyou share the resource with.
The two actions above take place simultaneously in tiCrypt.
info
The resource keys apply to all tiCrypt objects:
- Files
- Groups
- Drives, Etc.
- Keys prevent access to the drive.
- Only the resource owner is allowed to share the resource in the first place.
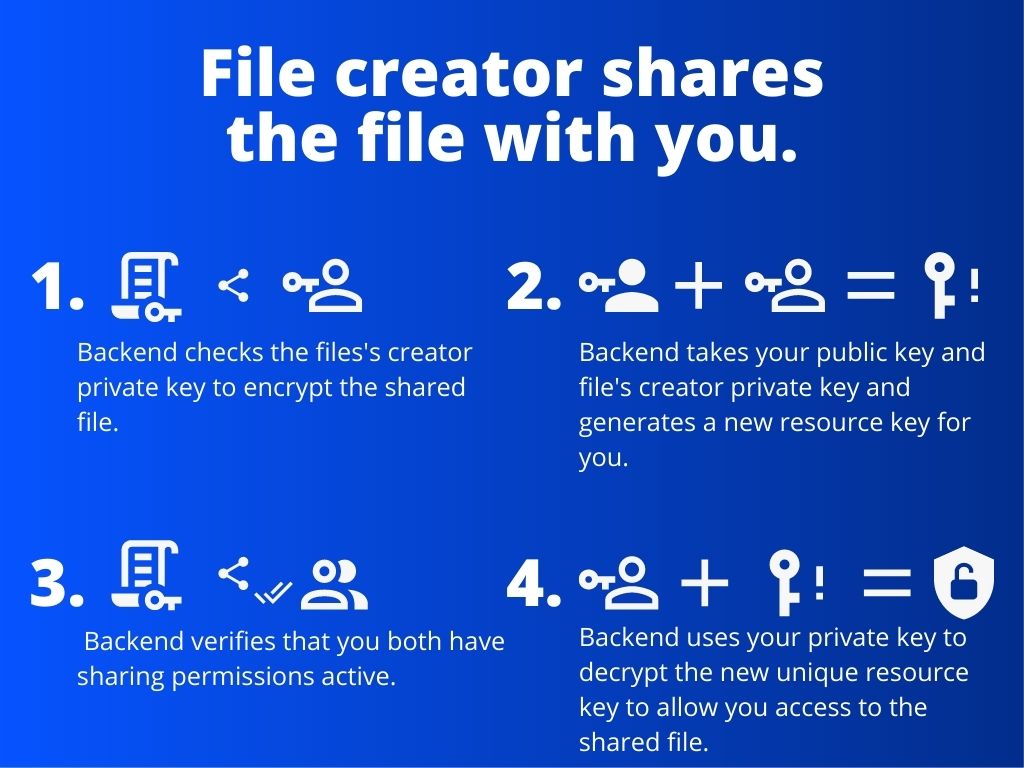
1. The creator of the file shares the file with you.
- The backend checks the user who shared the file's
private keyto encrypt the sharing file. - The backend takes your
public keyand the user who shared the file'sprivate keyand generates a newresource keyfor you. - The backend verifies that you both have
sharing permissionsactive. - The backend uses your
private keyto decrypt the new uniqueresource keyto allow you access to the shared file.
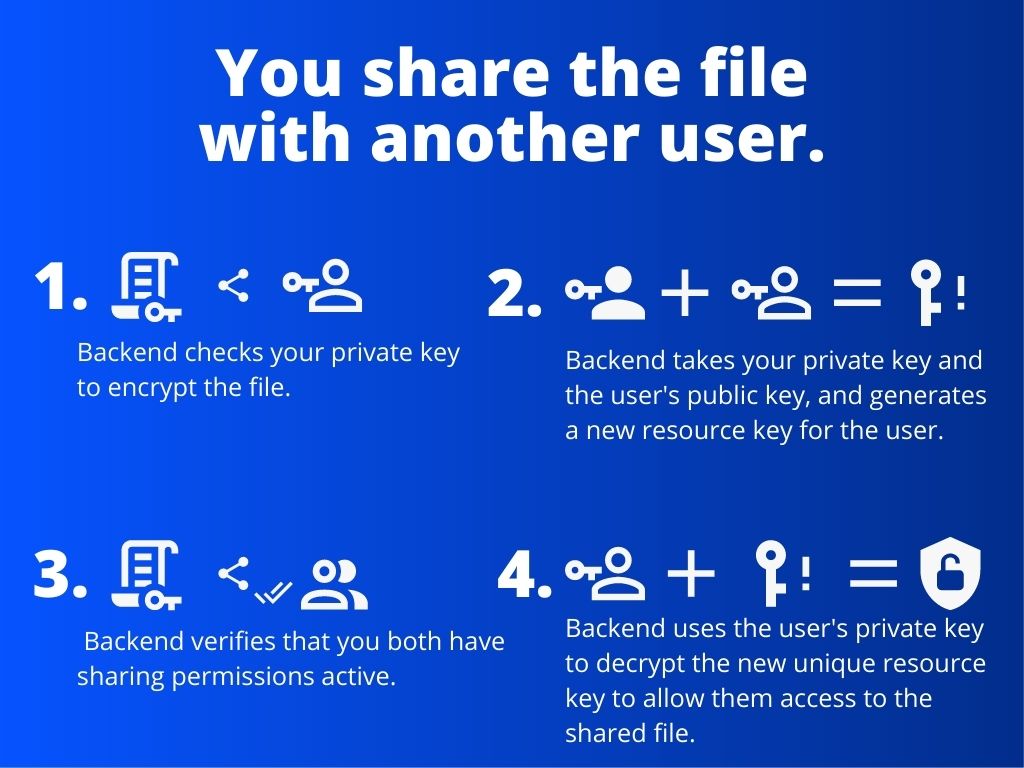
2. You share the file with another user.
- The backend checks your
private keyto encrypt the file. - The backend takes your
private keyand the user'spublic keyyou would like to share the file with and generates a newresource keyfor the user. - The backend verifies that you both have
sharing permissionsactive. - The backend uses the user's
private keyto decrypt the new uniqueresource keyto allow them access to the shared file.
Both steps above happen under 0.1 milliseconds.
- Resource keys are managed using the
public keyof the users.
note
- The private key is never "naked" anywhere in the backend, tiCrypt system, local machine, or on the browser.
- Keys are kept in memory for the smallest amount of time possible (under 0.1 milliseconds).
caution
You cannot share if you do not have your own public/private keys.