tiCrypt Overall
tiCrypt is a complete cryptographic private cloud solution built by Tera Insights LLC, that allows organizations to be CMMC 2.0 and NIST 800-53 compliant.
- The beginnings of tiCrypt.
- Introduction to cryptography.
Early Beginnings
In 2012, Dr. Alin Dobra worked as an Assistant Professor in the Department of Computer & Information Science & Engineering at the University of Florida. He was asked to devise a solution that would be FISMA-compliant, allowing better secure research for sensitive academic projects within the university.
In those days, the conventional pathways of Cloud computing and Access Controlled Lists stood as the pillars of security. Yet, the limitations of these approaches became starkly evident. Across the expanse of American academia, universities struggled to sustain a mere handful of projects due to the exorbitant resource costs involved – a stifling bottleneck that demanded innovation.
From the crucible of this challenge, a pioneering concept was conceived: tiCrypt emerged, a creation that defied the norms of its time. The birth of tiCrypt caused a seismic shift in research computing, introducing an unprecedented principle-based solution. What set tiCrypt apart from its peers was its foundation rooted entirely in public-key cryptography, a technology as intricate and formidable as the digital currency Bitcoin itself. The audacity of this idea lay in its inherent safeguarding nature – hacking tiCrypt would be as difficult as hacking Bitcoin, an attempt that remains impossible to this day.
Since 2012, the Tera Insights team has spent over 13 years meticulously developing and perfecting the product without altering its highly secure public-key cryptography mechanism.
As a result, tiCrypt quickly became a fully compliant solution from every technical perspective.
Today, as the sun sets on the passage of time since its inception, tiCrypt stands resolute – an eternal guardian of secure research, an emblem of innovation unaffected by market fluctuations, government regulations, or shifts in the US economy.
Dr. Dobra's vision, harnessed through technical knowledge, yielded a legacy that inspires and safeguards the large American Academia in pursuing excellence without bounds or constraints.
Introduction to Cryptography
Cryptography has existed since Ancient Egypt. Today, it refers to the practice and study of techniques for secure digital communication.
The foundational cryptography technique is the symmetric or “secret key” system. To use this technique, a user converts their data into a disguised code called a cipher code. During this process, the user also creates a separate digital key that can restore the cipher code to its original data. This process of scrambling data is known as encryption.
The cipher code and the key are sent to an intended recipient, who can decrypt the data. The problem with this method is that a third party can intercept the cipher code and the key, thus giving them access to data they shouldn’t have. To address this, cryptologists came up with the asymmetric system.
In this method, every user possesses both a public and a private key. The public key can be shared, whereas the private key must be protected. A sender requests the public key from the intended recipient, encrypts the message and sends it. When the recipient receives the message, only their private key can be used to decrypt the message. This ensures that even if a third party intercepts the message, they cannot decode it without the recipient's private key.
The following diagram displays how public and private keys from two users can be used for encryption and decryption. Alice and Bob cannot encrypt or decrypt on their own. Once they exchange public keys, they can "combine" them with their private keys to generate the "password."
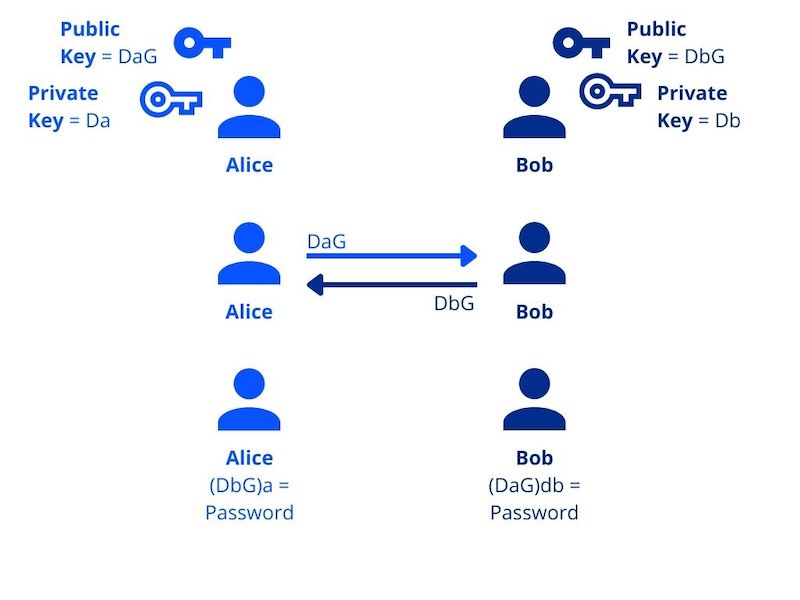
In tiCrypt, every user is given a public and private key. All users must log in to the system using their private key. Every time a user adds a resource to a group, behind the scenes, the user encrypts the resource, and when the recipient wants to view it, they use their private key.