tiCrypt Secure Clusters Architecture
Overview
It may be the case that a user needs to connect multiple Windows virtual machines. tiCrypt supports this feature with something called constellations.
Constellations are a network of virtual machines that can be created and managed through the tiCrypt interface. Any user that has the permission to manage the VM Brick of VM; the corresponding worker VMs is eligible to create a cluster.
The image below depicts the tiCrypt Constellation Architecture. This diagram is referenced below.
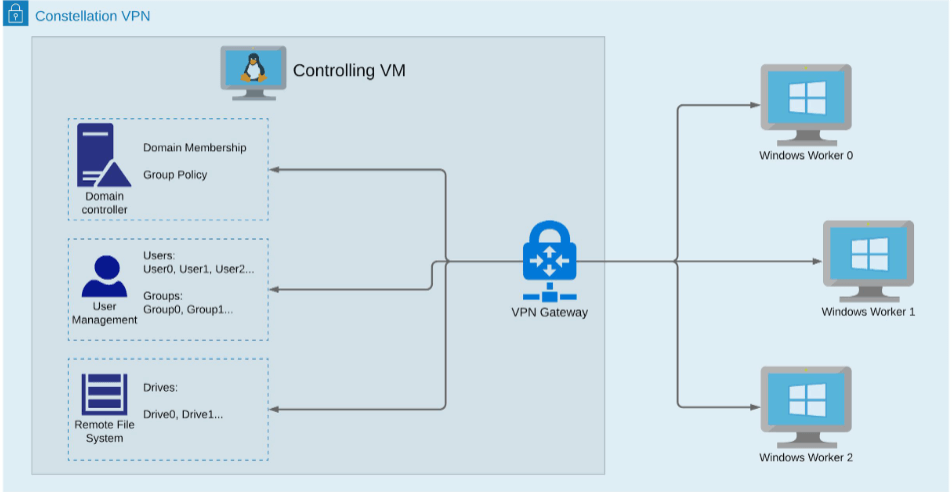
Windows Workers Virtual Machines
Windows Workers are not different from the normal tiCrypt VMs and they can be utilized for the same purposes. The advantage to these VMs is that they can be clusterized. This allows the user to distribute tasks among different machines while sharing a common file system and user management. These machines can also act as servers inside the constellation; because the constellation's internal traffic is isolated from the rest of the system, it allows for intercommunication among these machines.
How to start up a cluster
- The first requirement when creating a cluster is to have a special brick that is prepared to act as a Controlling VM.
- When a machine is started based on that brick, the system detects it has such capabilities and through a very simple interface, it allows the user to add VMs to the constellation.
- The created VM then goes through an initialization mechanism of about 5 minutes, then the user can see their new VM in the constellation management panel and connect to it through Remote Desktop Protocol (RDP).
Initialization Mechansim
The diagram below references the steps to follow.
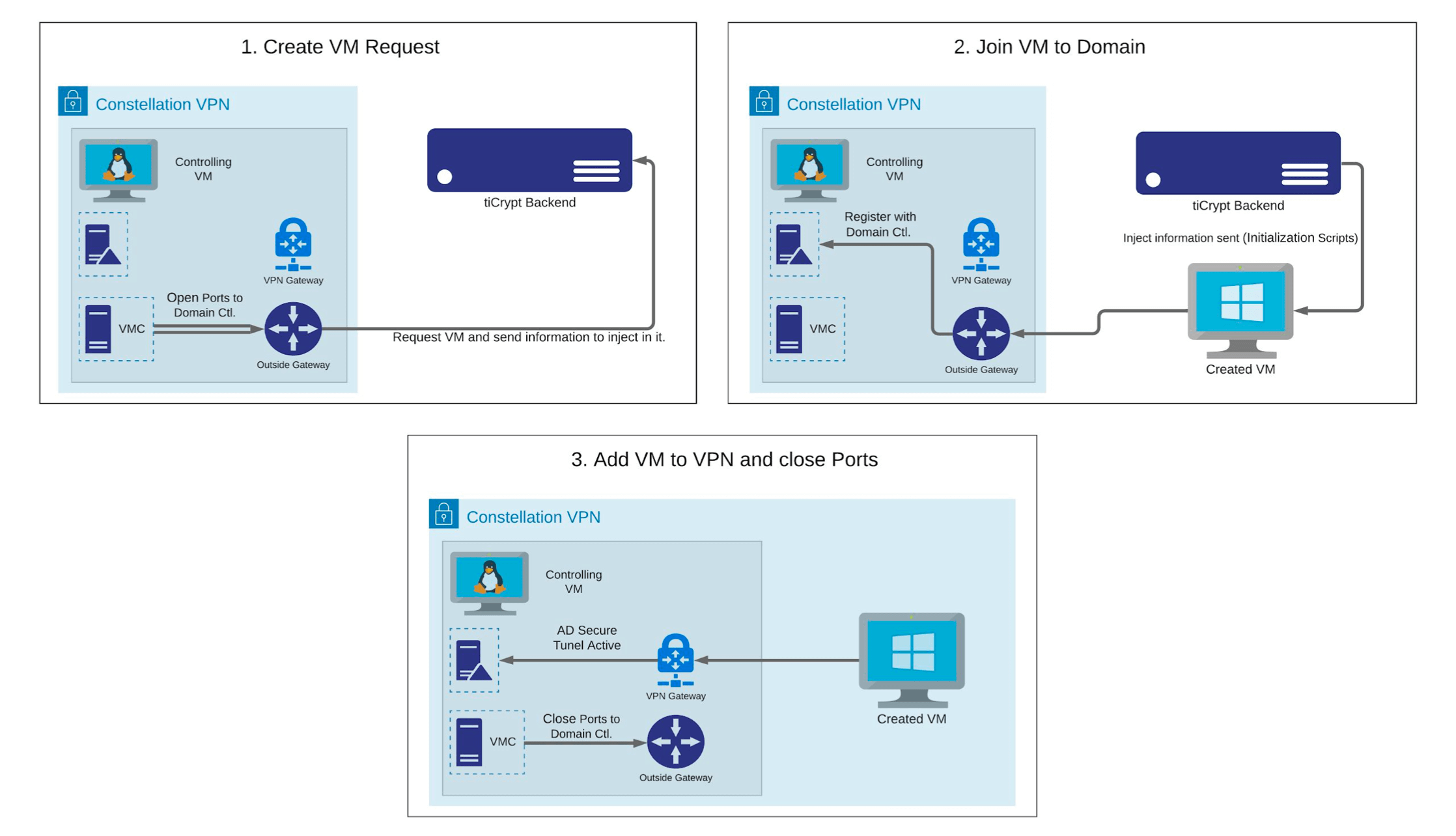
- The first step in the initialization of a constellation VM is when the VM controller requests a new VM from the tiCrypt backend based on the specifications given by the user. Immediately after, the VM Controller opens certain external ports required for a VM to join the domain.
- After that, before the requested VM registers with the system, we inject several scripts into it through a mechanism provided in the new VM Controller Stub. These scripts perform the joining process while restarting the computer several times as necessary.
- Then, finally, the Controlling VM gets access to the newly created VM, adds it to the VPN, and closes the ports it opened previously.