Introduction
tiCrypt Overview
tiCrypt is a complete cryptographic private cloud solution that allows organizations to be CMMC 2.0, NIST 800-53, NIST 800-171-172 and ITAR compliant.
There are two primary parts of tiCrypt: the front end and the back end.
The front end is the UX and user-facing portion of the tiCrypt software. The back-end is the admin esoterical system portion of the tiCrypt software.
Introduction to Cryptography
Cryptography, by definition, is the study of secure techniques that allow only the sender and intended recipient of a message to view the contents.
The word 'Cryptography' is derived from the greek word Kryptos which means hidden. This is similar to encryption, which is the act of scrambling up ordinary text and then unscrambling it to understand the content of the message. When transmitting any type of data, the most common use of cryptography is the act of encryption and decryption.
Encryption & Decryption Explained
By definition, encryption means to conceal or convert data into a form of disguised code, also known as cipher code.
Decryption is the exact opposite; it transforms a code from cipher code into intelligible code.
The simplest form of cryptography uses the symmetric or the "secret key" system. This means the data is encrypted using the key, and both the encoded message and the key are sent to the receiver.
The receiver can then decrypt the message using the key. The issue with this method is that if a third party intercepts the message and the symmetric key before it gets to the receiver, they can decrypt the message.
It is simply not safe enough.
To address these issues, cryptologists came up with the asymmetric system. For this method, every user has both a public and a private key. The public key can be shared, whereas the private key must be protected. A sender requests the public key from the intended receiver, encrypts the message and sends it. When the recipient receives the message, only their private key can be used to decrypt the message. This means that even if a third party intercepted the message, there is no possible way for them to decode it unless they have the recipients' private key.
The following diagram displays how public and private keys from two users can be used for encryption and decryption. Alice and Bob alone cannot encrypt or decrypt. Once they have each other's public key, they can "combine" it with their private key which grants them the "password."
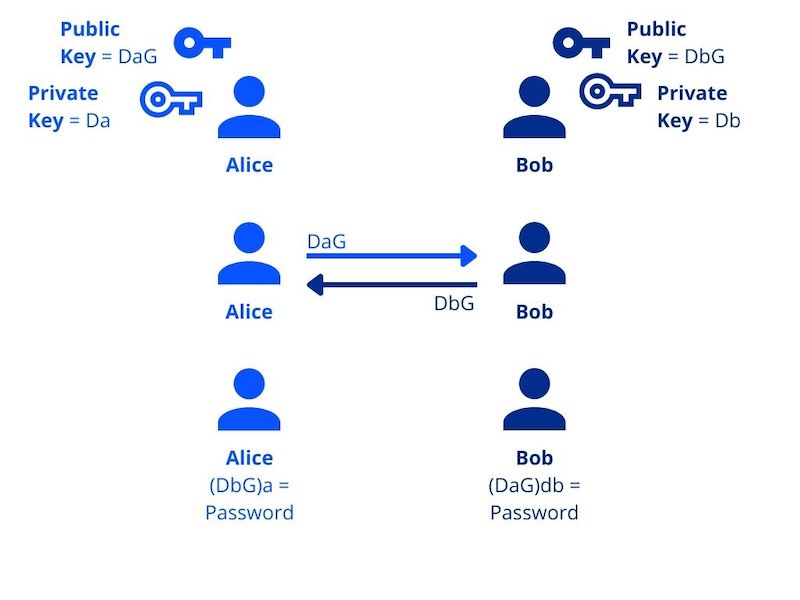
In tiCrypt, every user is given a public and private key. All users must log in to the system using their private key. Every time a user adds a resource to a group, behind the scenes, the user encrypts the resource, and when the recipient wants to view it, they use their private key.
For the Users
Vault
The Vault tab provides the functionality required for ad-hoc sharing, secure file preview, group sharing, and other storage functionalities. It is designed for users and researchers to transfer files securely into the system. The vault oversees current users, groups, and projects and has the functionality of creating inboxes for external contributors.
The inboxes' backbone is public key cryptography, as data confinement is achieved using independent keys for each resource. Critical management is avoided in tiCrypt globally through public key cryptography.
Virtual Machines
The Virtual Machines tab allows users to start and manage Virtual Machine configurations and drives. Users spend most of their time in the virtual machine environment.
Virtual machines allow secure computation by upholding security through isolation. Each time, the VMs securely spin up new images of the underlying OS to avoid carrying over any chance of risk from the previous execution. The access to VMs is also PKI-based, allowing the VMs to be owned by users, not admins.
Auditing is the most significant reporting feature, as every action is tracked whenever files move in and out of the VM. This action gives a clear history of what happened, allowing users to verify the VM if required. VMs allow complete ownership to researchers as no tool/ mechanism restrictions are in place; instead, all the security is upheld at the tiCrypt level with no compromise to provide secure processing.
My Profile
My Profile iterates a user's ability to achieve ownership and self-management. In particular, the user profile encapsulates the various actions a user can do based on a given set of permissions:
- Drives: Create/ Manage drives mounted on to VM secured by encryption abilities.
- Teams: Belong to a team and communicate with the team members.
- Groups: Allows the creation of a collective to assist collaboration, a group per se for easy assignment to projects, and dealing with users with given constraints.
- Mailbox: A bookkeeping feature to quickly navigate to inbox directories and exposes an access point to allow one to bring data in using web interfaces.
- Projects: Belong to a project and communicate with the project members.
- Certifications: This is where one can relay restrictions as needed of a special assessment to permit access to, say, a particular project. This modal iterates all the user's certifications and allows one to manage their validity in tiCrypt here.
- Permissions: This is the knowledge dump on actions one is authorized to do.
- Tasks: This is a view of recently completed/ running tasks- a modal essentially tracking the progress and relaying it to the user.
- User Menu: Place to edit and manage one's profile and look over the resource consumption of the team with its limits.
- Notifications: Allows viewing of all actions during the user sessions, tasks, and log history.
For the Admins
Management
The Management tab serves as permission control and management of the users. Here, admins can develop the user profiles and their teams, the workflow structure of the projects, the virtual machine management, and system back-ups. In tiCrypt, the management tab may be one of the most complex tabs due to its functionalities and effect on the system. Most of the admin work is taking place in the management tab.
User Management
A feature that allows the administrators to manage users' team ownership and their authentication and authorization access to tiCrypt. It allows an admin to grant users' activation status and belonging to the collaboration collectives like teams and projects. Permissions are used here as access control lists over the underlying PKI. All the actions for this feature are not required to be done one at a time; but instead as bulk edits, and that's a capability that tiCrypt provides.
Team Management
Team Management allows for resource constraints on a collection of users. This management belongs to the administrators, enabling one to add/ remove users and edit to the concerned resource limits.
Project Management
Project Management coordinates the trade-off between friction and ease of access; projects are the tool that allows resources to be tagged against them and then enable authorization to all the users in that instance. Essentially, a security tagging mechanism allows for any resource, even drives or VMs, to be protected and only shared with other users who are part of that project. Once a project label has tagged a resource or group, the way it can be manipulated or accessed is significantly restricted.
Backups
As the name suggests, this feature allows admins to create a backup of collections of users/projects/teams specified by domains. This action can be executed incrementally or as a full backup, allowing for a checkpoint mechanism with the encryption at its root.
Escrow
All tiCrypt resources are encrypted under PKI. At its core, each user has a private key that can be used to decrypt the user's copy of the resource encryption key. Should a user lose their key, the data (files, messages, drives) is impossible to recover, given the theoretical limits the encryption entails. To allow users to regain access to their data in case of private key loss or to enable data access for law enforcement in extenuating circumstances, tiCrypt provides a sophisticated key-escrow mechanism that can recover a user's private key and thus re-establish access. This result is achieved by the idea of segregation of duties and posing a limit to one's admin power- essentially imposing increased friction to reduce the chance of fraud.