General Cryptography
What is Cryptography?
Cryptography, by definition, is the study of secure techniques that allow only the sender and intended recipient of a message to view the contents. The word Cryptography is derived from the greek word Kryptos which means hidden. This is very similar to encryption, which is the act of scrambling up ordinary text and then unscrambling it in order to understand the content of the message. When transmitting any type of data, the most common use of cryptography is to encrypt and decrypt.
What does it mean to Encrypt and Decrypt?
By definition, encrypt means to conceal or convert data into some form of disguised code, also known as cipher code. Decrypt is the exact opposite; it transforms a code from cipher into intelligible code. The simplest form of cryptography uses the symmetric or "secret key" system. This means that data is encrypted using the key, and then both the encoded message and the key are sent to the receiver. The reciever can then decrypt the message using the key. The issue with this method is that if a third party intercepts the message and symmertic key before it gets to the receiver, they can decrypt the message. It is simply not safe enough.
To address this uses, cryptologists came up with the asymmetric system. For this method, every user has both a public and a private key. The public can be shared whereas the private key MUST be protected. A sender requests the public key from the intended receiver, encrypts the message and sends it. When the recipient receives the message, only their private key can be used to decrypt the message. This means that even if a third party interceptyed the message, there is no possible way for them to decode it unless they have the recipients private key.
The following diagram displays how public and private keys from two users can be used to encrypt and decrypt. Alice and Bob alone cannot encrypt or decrypt. Once they have each other's public key, they can "combine" it with their private key which grants them the "password."
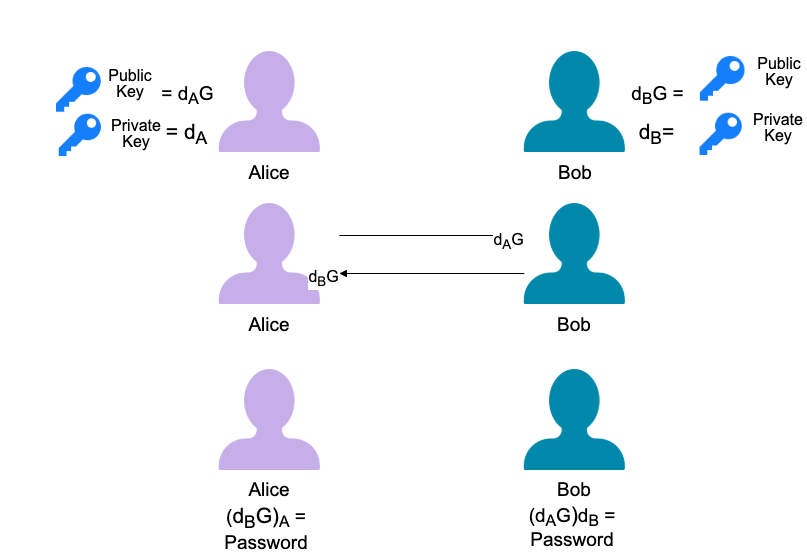
In tiCrypt, every user is given a public and private key. All users must login to the system using their private key. Every time a user does something such as sharing a file or adding resources to a group, behind the scenes, the user is encrypting the resource and when the recipient wants to view it, they use their private key.